A little housekeeping before we start
A lot of companies uses Active Directory (AD) to manage their user login and permissions. I’m sure you’re aware of this and its importance so I won’t really discuss the why you would want to learn about it, but here are some basics to get you started.
Active Directory is the main service that manages everything in your Windows environment. From users and computers, to DC servers, GPO and so many other integral things to your IT environment. There are a lot of things that integrate with Active Directory, but this topic will only discuss the basics. You will see learn more about AD’s integration with other services as we go along the course.
Topics Objectives
My goal in this topic is to show you how to install and Setup Active Directory on your Windows Server alongside some tips to help you create your own project. ( We will make the server into a domain controller). After that, I will talk about the basics on user management with AD Users and computers, Organizational Units (OU), Security/Distribution Groups.
This is quite a lengthy process, but I made sure to break it down into steps, so you can do it slowly, or skip ahead to the sections you want to learn. Also, setting up this server is integral to a fun experiment in later a Topic! Have fun learning! (Try to not copy pasta everything but adjust things up a little with my recommendation. And if you ever run into problems because of that, that’s even better for learning and troubleshooting!)
Part 1 – Installing Active Directory Domain Services (ADDS)+ Creating your Forest (Just primary Domain) and Promoting the server to be a Primary Domain Controller in your environment.
I have here a boring step by step stuff, with some remarks and advice, which I recommend reviewing for some of the notes and then watch this really cool video on how to do everything I say since it’s much easier visually. There are a few changes I have and some tips/note but this video is really good and it’s only 7mn:40s! (You can also check out this blog I found if you prefer that way – https://www.manageengine.com/products/active-directory-audit/kb/how-to/how-to-add-a-domain-controller-to-an-existing-domain.html (it’s pretty good)
These are the Boring Steps (no screenshots XD It was too many screenshots so I give up… Watch the video/Follow the blog I shared above, after you review the steps here). The notes here are things you want to know when Setting up Active Directory and Setting up your Domain Controller
Active Directory Domain Services Install
In Server Manager > Add roles and features > then in the Add Roles and Features Wizard > Click Next in the Before You Begin tab (make sure you have Static IP + All the updates installed on the Server) > in Installation Type, select Role based or feature-based installation > in Server Selection tab, select your server (which is only one for now) > in Server Roles, check Active Directory Domain Services and make sure the Include management tools is checked on the popup > then just Next, Next, till you’re in Confirmation tab > in Confirmation tab, you should check Restart the destination server automatically (to make your life easier) and then click on Install.
Promoting Server to a Domain Controller – Creating your Forest/Domain.
After installing ADDS and Restarting your Server. In Server Manager > in the Flag/notification button with ! > Click Promote this server to a domain controller > in the ADDS Configuration Wizard > Deployment Configuration tab, select Add a new forest (Since we are creating a new domain) -You can use any name you’d like for your domain and make it end with a .com/.net/.org/.local or whatever you like (ex: HomelabExp.net) > In Domain Controller Options, chose whichever Windows Server Version you want the domain to be able to operate in. In an older environment, there might be a Server with older Windows servers being used so you will pick that version, but at the very least you’d want 2012 R2, and preferably you’d always want the latest versions in your domain/forest. This option means that the domain will only work in Windows Server that have this version or newer, but for the lab, you can pick whatever lol. As for the Specify Domain controller capabilities, just check Global Catalog (GC) and uncheck DNS server (We will be setting one up in the next topic). The DRSM Password is what you use to get in the server after so make sure you remember (And of course, make a strong one if it’s going to be used for production) > in Additional Options, just go with what comes there since this is not really used nowdays> in Paths, you can change the destination folders for your database if you’d like. This is actually really important to note if you want to do backups and other stuff, but for now, you don’t really need to care > then Next > in the Prerequisites Check, you can just click Install after the check > your Server will restart automatically after Install > After the reboot, the screen at the bottom should say “Sign in to: (your domain name)”. For login in, you will be using the user “Administrator” and the new DRSM Password you set before.
Check it’s all good
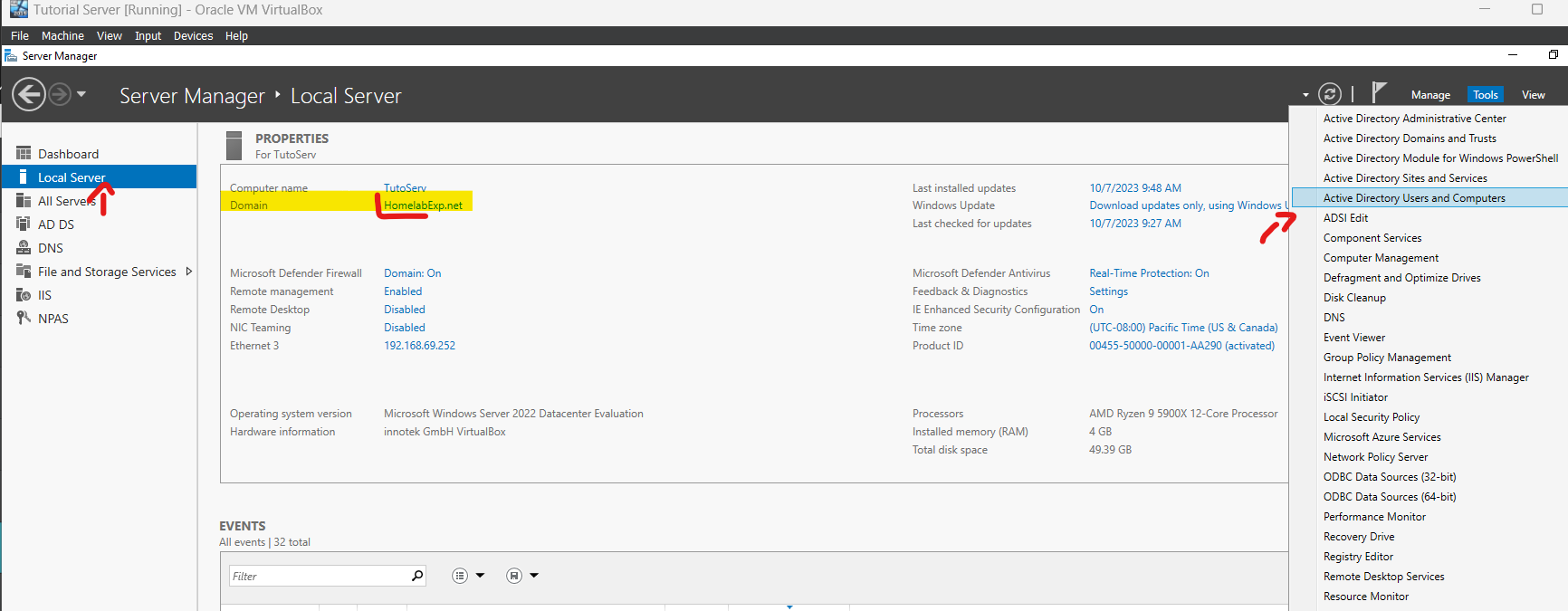
Now after the Install, if you go to the Local Server, it should show your Domain name. Also, if you go in the Tools menu, you should be able to see Active Directory stuff (you mostly care about Active Directory Users and Computers).
Part 2 -How to use Active Directory/the Basics of Users and Computer management with OUs, Security Groups and some other basics stuff and Tips
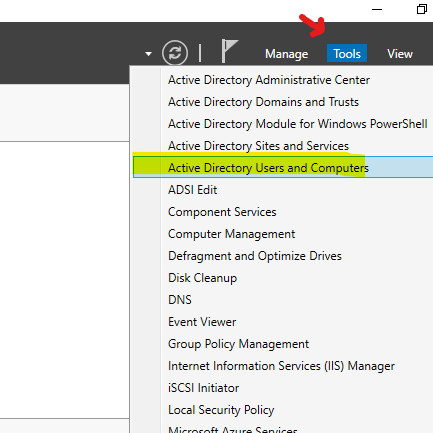
The main tool you will be using is Active Directory Users and Computers. This is where you will be doing most of the work to create and manage users and computers in your domain. To open AD Users and Computers, Just go to Tools and there, you can select Active Directory Users and Computers.
Organizational Units (OU) / Containers
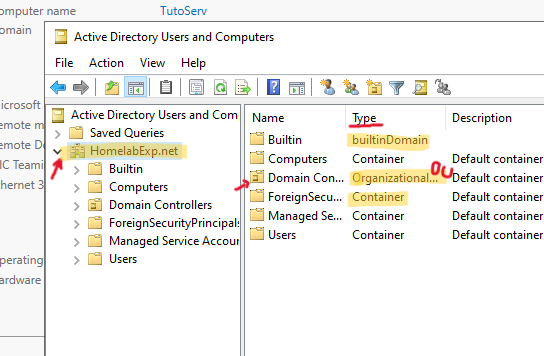
In Active Directory Users and Computers, You can Expand your Domain to see all the Containers and Organizational Units (OU), which are the Folder thingy you see under your domain. These OUs, as their name suggest, is a way to organize and sort your stuff (you will see more use for them on later topics as well, when we do GPO stuff). The way they are ordered/the hierarchy in which they are stored is important (but again, no need to care about much for now, just keep it in mind). Note that OUs and Containers are pretty much the same. OUs are just the stuff you created, but they function the same. You can tell the OUs from the tiny difference in icon.
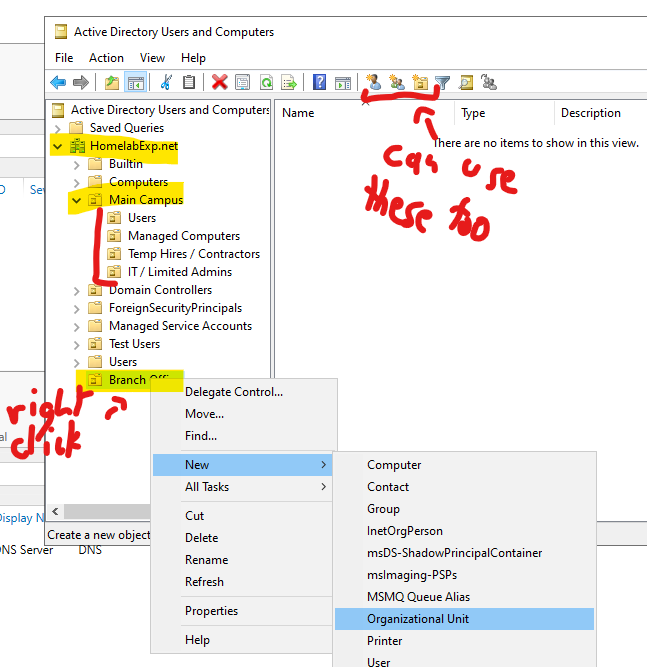
You can Right Click on any OUs, or even on your Domain Name to Create a new OU inside it. For your main OUs. I recommend Creating your OU from the Domain Name itself, to categorize your main organizations, and then making sub containers inside to manage users/computers and other things like in the example bellow.
Security Groups
The other VERY important part of user management in Active Directory are the Security/Distribution Groups. You’d mostly care about Security Groups and you can ignore the other option. For the Scope, you can leave on Global since we only have one domain anyway (No subdomains and not Azure AD joined)
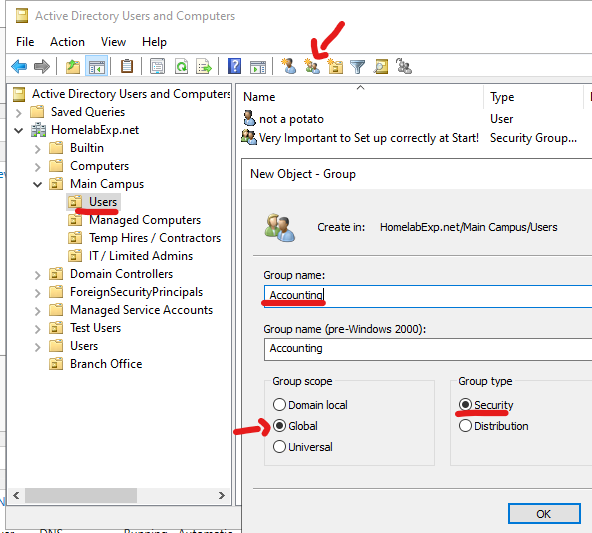
To Add Users to a Group, You can either go in the Group itself and look for users (This is also how you’d check if certain users have the appropriate privilege). Or you can just right click on the user itself, and click on Add to a group, and then search for the group.
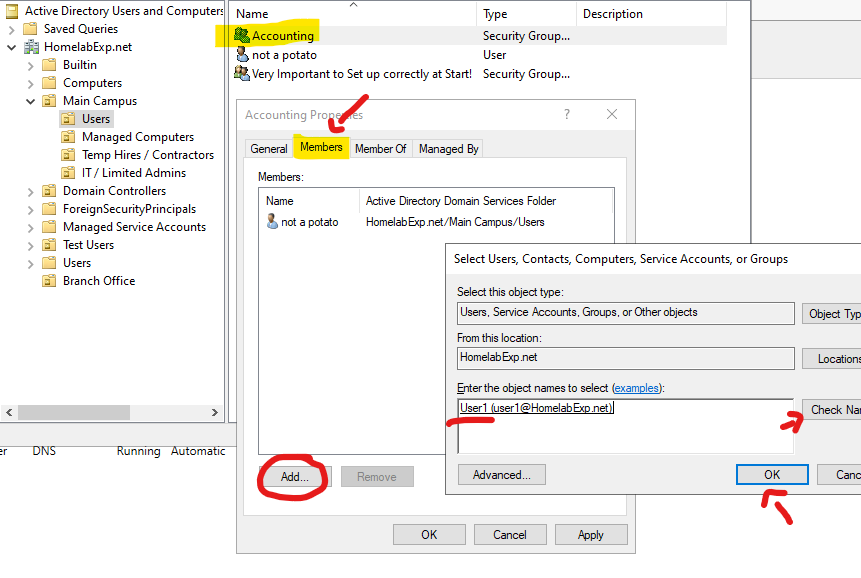
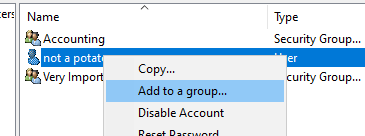
Using Security Group is the most effective way to manage a group of users/computers. You really want to make sure you plan this correctly at the beginning of deploying your Domain / You can later plan to reorganize things to make managing your users simpler and more effective/efficient.
This is one of those things that’s more planning and takes 5mn to implement, but will save you soooo much time and boring work if you implement correctly.
Some of the Typical way Security Groups comes in really really handy is when you give File permission and Applying GPO (More about this on a later Topic). Essentially, instead of giving permission and applying GPO for each individual users, you just assign them to a Group and they will get everything they need automatically. That way, when you create a new user/promote someone, you can just add/move them to different groups and they will get all the File permissions and appropriate level of privilege they should have!
Having these Set up Properly is a really good way to easily apply the Least Privilege Rule in IT, since you won’t have to deal with multiple users, but just one group. So again, this’s really important to plan out when you set up your DC, especially in a company/org that has multiple users.
Users (Object)
Last but most importantly not least, Users (Object). I put User stuff last since you probably know about this already, but for those who don’t/wants a review, here we go. (Objects -stuff you manage in your Active Directory, like Users, Computers, Servers, Printers, etc..). I will only mention user stuff here since they what you will most likely deal with. You can Create new users from either right clicking on a container > New > User. Or, you can open a container and then click on the User Icon thingy at the top menu.
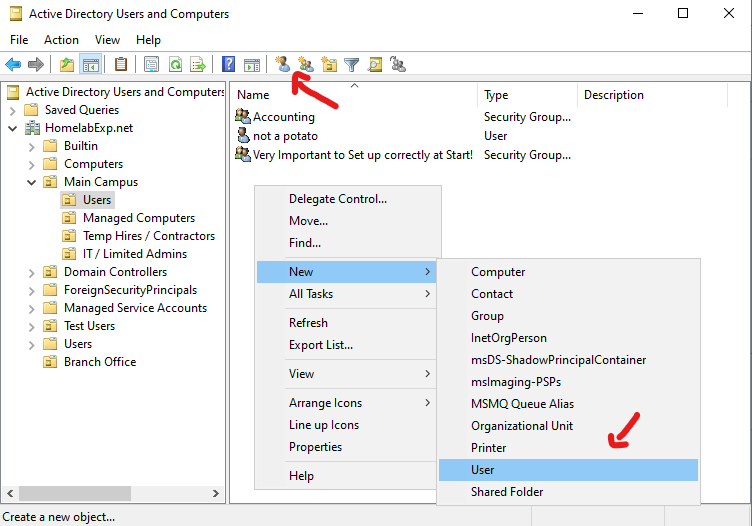
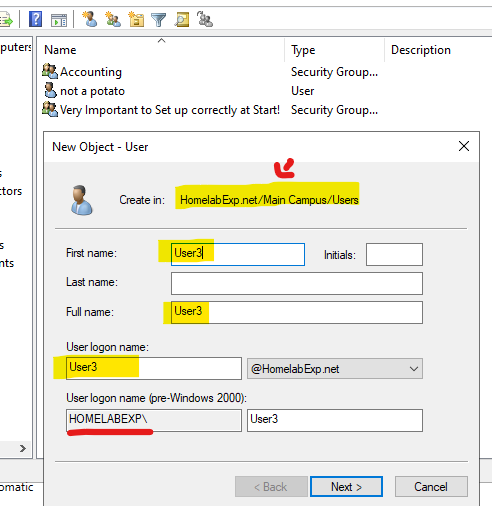
This is what it looks like when you Create a new User. Note that it shows the path for the container in which you create the user. This is good to know when you create a user in the right OU (for GPO stuff -later). Also, if you operate in a multi domain environment/need to differentiate between local and domain users, you can use the User logon name – DomainName\user (ex: homelabexp\user3) You mostly use this when signing as Administrator when you RDP into them and you want to sign in as local/domain, so you specify (for local login, you use .\user -ex: .\nyght)
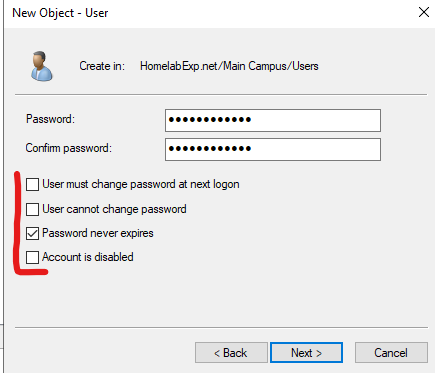
For the user Password. Typically (in production use), You either leave it on default option, which is User must change password at next logon, and you send the temp password to your user for them to change. Or, you set a good password yourself and then securely send them the password. If you do this, the password will expire in 42 days (default password GPO settings, more on this on a later Topic). BUT, for our lab testing, you can make it so it never expires for convenience.
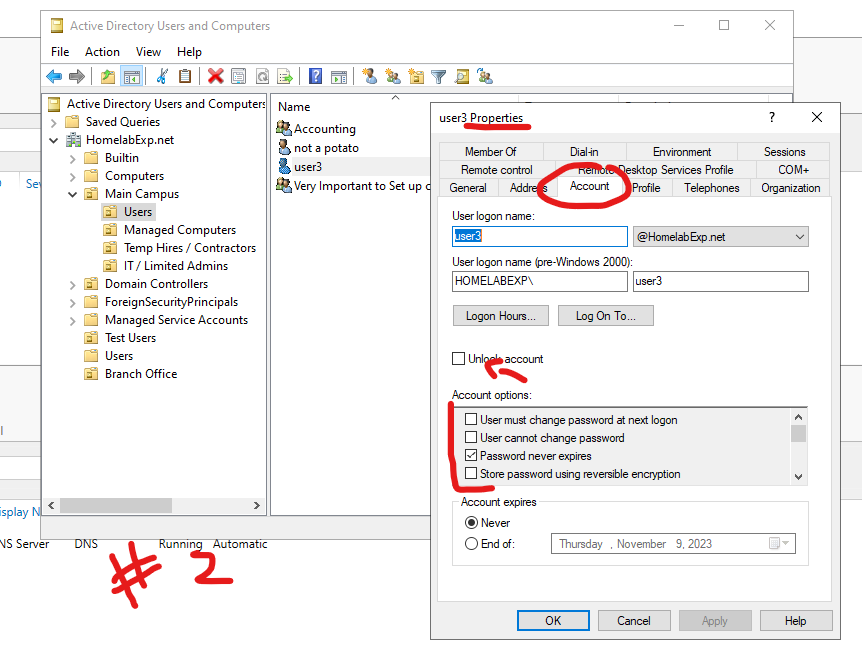
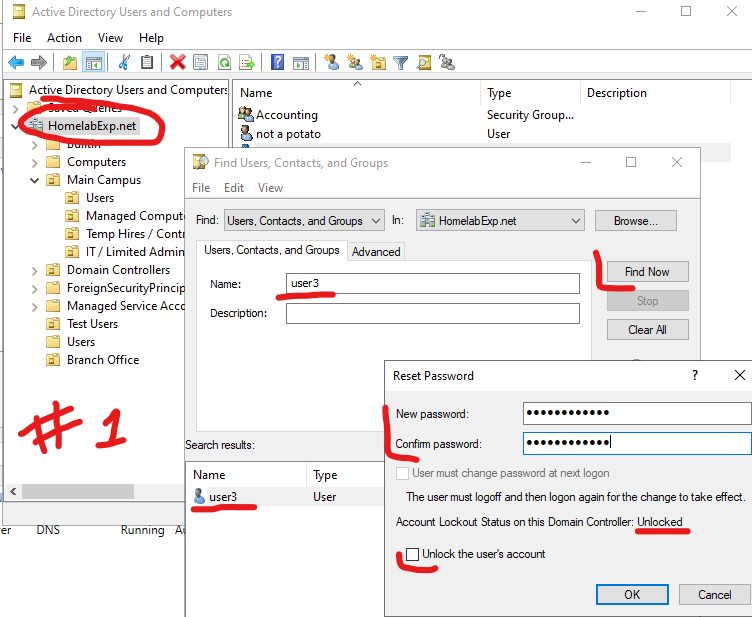
For the Typical user account unlock stuff, you can either unlock from user property by right click on user > property > Unlock and then check on User must change password at next logon. OR, you can right click on your domain > select Find (second option) > Type the user name and then click on Find Now > the User should show at the bottom. Right click on the user to Reset password and you can reset their password for them. You can also double click on the user to get in User Properties here.
Before you leave, here are some good to know Tips you might need for your stuff.
- Tips 1 -in AD Users and Computers, You can check the Advanced Features, which is off by default.
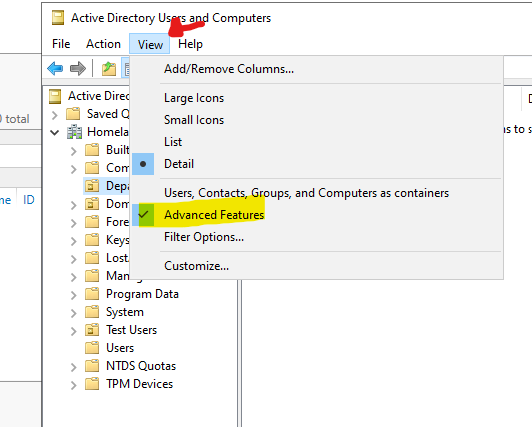
Having the Advanced Features will allow you to remove the protection from the OUs you accidentally create and some other stuff. But again, do leave it off after you finish since it’s better for others to have less things to mess up XD…
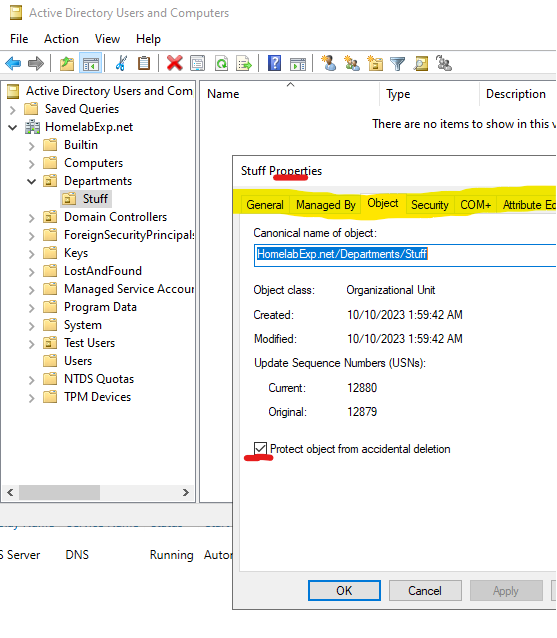
This is what it would look like if you don’t have the feature turned on /the default look. And again, do turn it off after you finish setting up the essentials/ done using the extra features since it’s better with the default view.
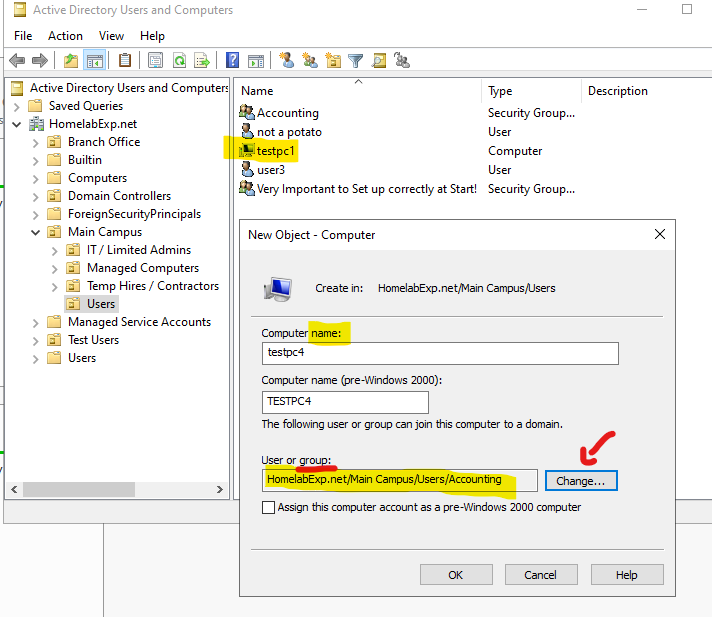
Tip 2- You can pre-create a new Computer object and assign it to a group, and then when you setup a new computer, you can give it the name you created to have that computer have all the GPO stuff it needs (it’s good to set up when you deploy lots of desktops!)
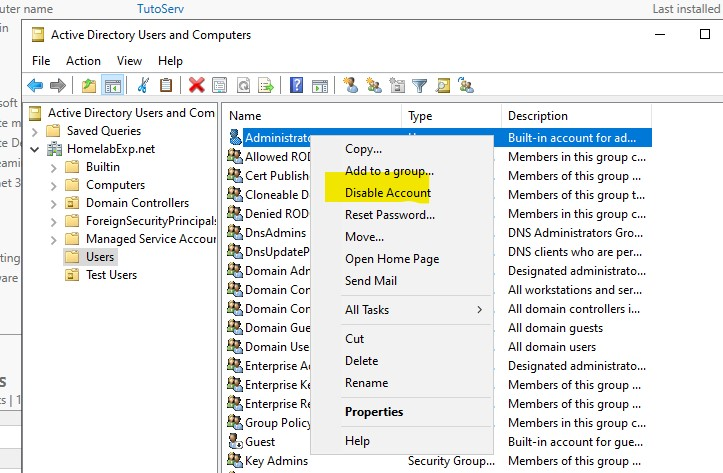
Tip 3 -Another Tip for Security in your environment is to Disable the Admin Account, and instead Create another Admin with a different name. But again, no need to worry about this for the lab. I will probably do some Basics Security Topics later but that’s gonna be Later Later XD, so I’ll try to give some along the way. (note that you want to make sure the new admin account you create is part of all the groups necessary + it’s good to keep at least 2 admins account, so you don’t accidentally get locked out of your DC server XD -This is one of the scariest rookie mistake ever..)
Closing words
With that, you should have all the basics you need for using and managing Active Directory. I highly recommend you have a look around and create an organizational template (with OUs, Security Groups and some test users) of your choice. There will be a ‘little’ fun Experiment for something using those on a later Topic with GPO stuff and Terminal Server, and it’ll be more interesting for you to work with your own Setup!
I really hope you now have a better understanding on how things works in Active Directory, with Organizational Units (OU), Security Groups and general user management. There will be more application with this to show you more about the reason why you want to properly organize things, but that’s all the essentials you need to know.
If you’ve reached this far and tested things on your own, I hope you had fun Learning and Testing things out! And thank you for Learning with me here :3 huehue
PS. With how much work it takes to make these blogs, I know why people don’t make documentations for these XD -aaahhhh
-Nyght